问题导读
1.Docker Registry的作用是什么?
2.Docker Registry支持哪些存储方式?
3.Docker Registry多实例需要保持哪些数据一致?

【编者的话】Docker Registry用来存储和管理Docker Image, 本文说明如何基于Docker Registry(V2)构建安全可靠的Docker Registry。
Docker Registry安全TLS需获取证书, 建议从CA机构申请。信任域内可以使用自签名证书:
[mw_shl_code=bash,true]mkdir -p certs && openssl req \
-newkey rsa:4096 -nodes -sha256 -keyout certs/domain.key \
-x509 -days 365 -out certs/domain.crt[/mw_shl_code]
注: Common Name输入Docker Registry使用的域名<docker_registry_domin>
注: 如果使用自签名证书,使用Docker Registry的Docker机需要将domain.crt拷贝到
/etc/docker/certs.d/<docker_registry_domin>/ca.crt,然后重启docker同时将domain.crt内容放入系统的CA bundle文件当中,使操作系统信任我们的自签名证书。
CentOS 6 / 7中bundle文件的位置在/etc/pki/tls/certs/ca-bundle.crt:
[mw_shl_code=bash,true]cat domain.crt >> /etc/pki/tls/certs/ca-bundle.crt[/mw_shl_code]
启动Docker Registry容器使用证书开启TLS:
[mw_shl_code=bash,true]docker run -d -p 5000:5000 --restart=always --name registry \
-v /path/to/certs:/certs \
-e REGISTRY_HTTP_SECRET=mytokensecret \
-e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \
-e REGISTRY_HTTP_TLS_KEY=/certs/domain.key \
registry:2[/mw_shl_code]
Basic Authentication创建账号密码:
[mw_shl_code=bash,true]mkdir auth
docker run --entrypoint htpasswd registry:2 -Bbn <testuser> <testpassword> auth/htpasswd[/mw_shl_code]
启动Docker Registry容器设置启动Authentication:
[mw_shl_code=bash,true]docker run -d -p 5000:5000 --restart=always --name registry \
-v /path/to/auth:/auth \
-e "REGISTRY_AUTH=htpasswd" \
-e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" \
-e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd \
-v /path/to/certs:/certs \
-e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \
-e REGISTRY_HTTP_TLS_KEY=/certs/domain.key \
registry:2[/mw_shl_code]
使用Docker Registry的Docker机需要使用账号密码登陆:
[mw_shl_code=bash,true]docker login <docker_registry_domin>[/mw_shl_code]
Docker Registry可靠性存储Docker Registry支持多种存储方式:
- inmemory:A temporary storage driver using a local inmemory map. This exists solely for reference and testing.
- filesystem:A local storage driver configured to use a directory tree in the local filesystem.
- s3:A driver storing objects in an Amazon Simple Storage Solution (S3) bucket.
- Azure:A driver storing objects in Microsoft Azure Blob Storage.
- rados:A driver storing objects in a Ceph Object Storage pool.
- swift:A driver storing objects in Openstack Swift.
- oss:A driver storing objects in Aliyun OSS.
我这里采用Filesystem Storage Driver + MooseFS:
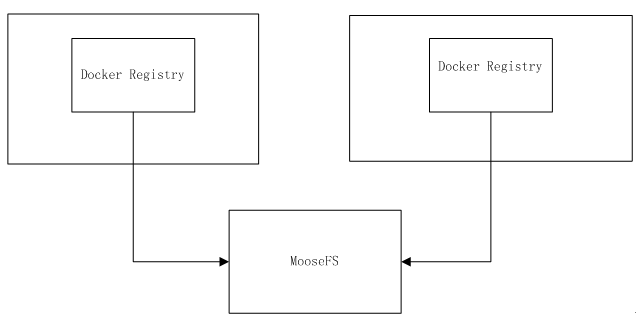
搭建MooseFS,然后文件系统挂载到Docker Registry节点, Docker Registry将数据存入MooseFS文件系统。
启动Docker Registry容器挂载Volume:
[mw_shl_code=bash,true]docker run -d -p 5000:5000 --restart=always --name registry \
-v /path/to/data:/var/lib/registry \
registry:2[/mw_shl_code]
集群Docker Registry多实例需要保持以下数据一致:
- Storage Driver
- HTTP Secret
- Redis Cache (if configured)
Docker Registry多实例可以主备或者负载分担,其中负载分担方式需要保证一次docker push/pull都只是和一个Docker Registry实例交互,比较简单的做法可以是基于源IP做会话保持, 以haproxy为例:
[mw_shl_code=bash,true]frontend https_frontend
bind *:443
mode tcp
default_backend docker_registry
backend docker_registry
mode tcp
balance roundrobin
stick-table type ip size 200k expire 30m
stick on src
server s1 docker_registry_server1:5000
server s2 docker_registry_server2:5000[/mw_shl_code]
注:在每个节点上Docker Registry容器启动方式如下:
[mw_shl_code=bash,true]docker run -d -p 5005:5000 --restart=always \
-v /home/docker_registry:/var/lib/registry \
-e REGISTRY_HTTP_SECRET=watokensecret \
-v /home/docker_registry/auth:/auth \
-e "REGISTRY_AUTH=htpasswd" \
-e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" \
-e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd \
-v /home/docker_registry/certs:/certs \
-e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \
-e REGISTRY_HTTP_TLS_KEY=/certs/domain.key \
registry:2[/mw_shl_code]
作者简介
吴龙辉,现任网宿科技高级运营工程师,致力于云计算PaaS的研究和实践,活跃于CloudFoundry,Docker,Kubernetes等开源社区,贡献代码和撰写技术文档。
邮箱:wulh@chinanetcenter.com/wlh6666@qq.com
|
 /2
/2 